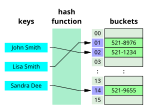
computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...
9 KB (1,130 words) - 16:51, 9 August 2024
hash map. Most hash table designs employ an imperfect hash function. Hash collisions, where the hash function generates the same index for more than one...
52 KB (5,873 words) - 00:21, 27 September 2024
the given hash value when one message is already known; finding any pair of different messages that yield the same hash value (a collision) is also infeasible:...
48 KB (6,228 words) - 13:24, 27 September 2024
cryptography, a collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision. This is in contrast...
17 KB (2,010 words) - 21:48, 17 May 2024
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S...
3 KB (464 words) - 13:15, 22 July 2024
SHA-1 (redirect from SHA-1 hash)
cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest...
51 KB (5,763 words) - 15:25, 17 September 2024
HMAC (redirect from Keyed-Hashing Message Authentication)
cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of...
18 KB (2,335 words) - 15:54, 19 September 2024
output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to...
50 KB (7,536 words) - 17:48, 18 September 2024
resistance, collision resistance, and pseudo-randomness. Pre-image resistance: given a hash h, it should be hard to find any message m such that h = hash(m)....
13 KB (1,811 words) - 20:15, 26 August 2024