trusted system is one that is relied upon to a specified extent to enforce a specified security policy. This is equivalent to saying that a trusted system...
17 KB (2,358 words) - 22:49, 30 July 2023
4+) Trusted Solaris Trusted UNICOS 8.0 (Rated B1) XTS-400 (Rated EAL5+) IBM VM (SP, BSE, HPO, XA, ESA, etc.) with RACF Examples of operating systems that...
4 KB (395 words) - 20:27, 25 August 2024
Trusted Computer System Evaluation Criteria (TCSEC) is a United States Government Department of Defense (DoD) standard that sets basic requirements for...
18 KB (2,101 words) - 21:38, 25 February 2024
Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and...
42 KB (5,186 words) - 19:55, 10 October 2024
The trusted computing base (TCB) of a computer system is the set of all hardware, firmware, and/or software components that are critical to its security...
12 KB (1,629 words) - 11:22, 20 August 2024
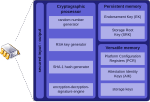
security against firmware attacks. Trusted Platform Module (TPM) was conceived by a computer industry consortium called Trusted Computing Group (TCG). It evolved...
79 KB (6,572 words) - 08:48, 6 October 2024
a trusted system external to one's mind. In this way, one can work on the task at hand without distraction from the "incompletes".: 14 The system in...
19 KB (2,199 words) - 09:39, 1 April 2024
operating system. Assuring that an authentic operating system starts in a trusted environment, which can then be considered trusted. Provision of a trusted operating...
13 KB (1,545 words) - 04:33, 31 August 2024
An honor system, trust system or honesty system is a way of running a variety of endeavors based on trust, honor, and honesty. The honor system is also...
6 KB (759 words) - 02:21, 19 October 2024
of the trusted system file. The Sasser worm spreads by exploiting a buffer overflow in the LSASS on Windows XP and Windows 2000 operating systems. "Configuring...
3 KB (246 words) - 13:41, 12 December 2023