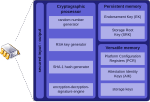
security against firmware attacks. Trusted Platform Module (TPM) was conceived by a computer industry consortium called Trusted Computing Group (TCG). It evolved...
79 KB (6,479 words) - 09:44, 29 August 2024
The Trusted Computing Group is a group formed in 2003 as the successor to the Trusted Computing Platform Alliance which was previously formed in 1999 to...
6 KB (610 words) - 20:27, 25 August 2024
of a trusted operating system with additional security capabilities not available to an unproven one. Intel TXT uses a Trusted Platform Module (TPM)...
12 KB (1,536 words) - 04:24, 30 August 2023
include Trusted Computing in their products if enabled. The U.S. Army requires that every new PC it purchases comes with a Trusted Platform Module (TPM)...
42 KB (5,183 words) - 05:13, 31 July 2024
directory structure, file names, modification timestamps or sizes. Trusted Platform Module (TPM) is a secure cryptoprocessor embedded in the motherboard that...
17 KB (2,147 words) - 01:55, 8 August 2024
Security Processor Trusted Platform Module ARM TrustZone NFC Secure Element Next-Generation Secure Computing Base "Introduction to Trusted Execution Environment:...
35 KB (3,185 words) - 05:13, 31 July 2024
Cold boot attack (redirect from Platform reset attack)
random-access memory, full disk encryption schemes, even with a trusted platform module installed are ineffective against this kind of attack. This is...
38 KB (4,246 words) - 03:19, 31 July 2024
Intel Management Engine (redirect from Trusted Execution Engine)
Samsung Knox Spectre (security vulnerability) Trusted Computing Trusted Execution Technology Trusted Platform Module Oster, Joseph E. (September 3, 2019). "Getting...
47 KB (4,481 words) - 19:47, 27 August 2024
cryptoprocessor Security token Transparent data encryption Security switch Trusted Platform Module Sommerhalder, Maria (2023), Mulder, Valentin; Mermoud, Alain; Lenders...
14 KB (1,564 words) - 02:37, 4 August 2024
VeraCrypt (category Cross-platform software)
physical access to the computer. VeraCrypt does not take advantage of Trusted Platform Module (TPM). VeraCrypt FAQ repeats the negative opinion of the original...
37 KB (3,203 words) - 21:06, 9 May 2024