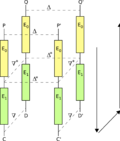
SHACAL-1 (originally simply SHACAL) is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher...
9 KB (903 words) - 07:08, 27 April 2022
Jung (December 2002). "Amplified Boomerang Attack against Reduced-Round SHACAL". ASIACRYPT 2002. Queenstown, New Zealand: Springer-Verlag. pp. 243–253...
9 KB (864 words) - 04:16, 17 October 2023
incorporated. The SHA hash functions have been used for the basis of the SHACAL block ciphers. Revision control systems such as Git, Mercurial, and Monotone...
51 KB (5,762 words) - 21:53, 22 July 2024
Shackle Island, Tennessee Shackled (disambiguation) Shackel Shakl SHACL SHACAL Shakal (disambiguation) Shekal This disambiguation page lists articles associated...
1 KB (193 words) - 19:49, 31 December 2020
NOEKEON NUSH PRESENT Prince Q RC2 REDOC Red Pike S-1 SAFER SAVILLE SC2000 SHACAL SHARK Simon Speck Spectr-H64 Square SXAL/MBAL Threefish Treyfer UES xmx...
98 KB (10,713 words) - 13:37, 29 July 2024
and SHA-2 are based on block ciphers which are also used independently as SHACAL, hash functions can be used to build block ciphers. Examples of such block...
50 KB (6,475 words) - 10:19, 23 June 2024
NOEKEON NUSH PRESENT Prince Q RC2 REDOC Red Pike S-1 SAFER SAVILLE SC2000 SHACAL SHARK Simon Speck Spectr-H64 Square SXAL/MBAL Threefish Treyfer UES xmx...
23 KB (3,307 words) - 18:11, 14 February 2024
Rijndael) Camellia: Nippon Telegraph and Telephone and Mitsubishi Electric SHACAL-2: Gemplus WHIRLPOOL: Scopus Tecnologia S.A. and K.U.Leuven SHA-256*, SHA-384*...
5 KB (537 words) - 15:11, 26 January 2024
NOEKEON NUSH PRESENT Prince Q RC2 REDOC Red Pike S-1 SAFER SAVILLE SC2000 SHACAL SHARK Simon Speck Spectr-H64 Square SXAL/MBAL Threefish Treyfer UES xmx...
15 KB (1,544 words) - 02:53, 7 June 2024
conventional mode of operation, without the same security guarantees; for example, SHACAL, BEAR and LION. Pseudorandom number generators (PRNGs) can be built using...
48 KB (6,228 words) - 21:37, 8 August 2024